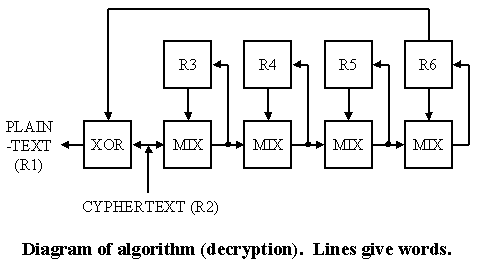
Although WAKE is described as an 'Autokey' cipher, it is in fact the same as a block cipher used in Cipher Feedback mode. The following sketch of the decryption mode, taken with the encryption mode sketch from the WAKE paper, highlights the similarity.

Here v is the input data, x is the stage register and y is the register associated with the previous stage. The output, z, provides the input to the stage register.
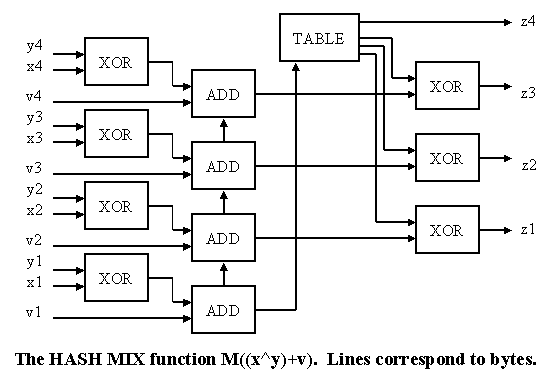
The function processes 4 words of data at a time. This could raise problems if the number of words is not a multiple of 4. However, a fairly compact piece of code deals with this and also problems that could arise concerning the amount of diffusion applied to the last few words to be hashed.
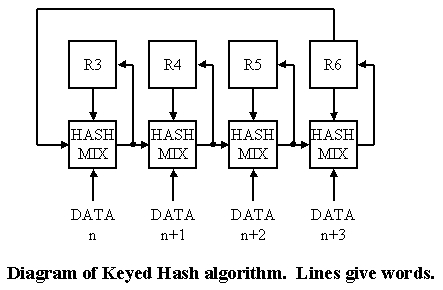
If we look at the C code for the hash function:
hash4(V, n, k, r, t)
long V[], n, k[], r[], t[];
{ long m, r3, r4, r5, r6, *e, mask = 0x00ffffff;
r3 = k[0]; r4 = k[1]; r5 = k[2]; r6 = k[3];
e = V + n - 3;
for (m = 0; m < 4; m++)
{ while (V < e)
{ r3 = (r3 ^ r6) + *V++;
r3 = (r3 >> 8 & mask) ^ t[r3 & 255];
r4 = (r4 ^ r3) + *V++;
r4 = (r4 >> 8 & mask) ^ t[r4 & 255];
r5 = (r5 ^ r4) + *V++;
r5 = (r5 >> 8 & mask) ^ t[r5 & 255];
r6 = (r6 ^ r5) + *V++;
r6 = (r6 >> 8 & mask) ^ t[r6 & 255];
}
V = e - 1;
}
r[0] = r3; r[1] = r4; r[2] = r5; r[3] = r6;
}
The operation on the last 4 words needs clarification.
The following examples show which words get hashed
(and how many times) v. the number of words processed:
|
Number |
e |
Hashed |
Hashed |
|
12 |
9 |
0 to 11 |
8 to 11 |
|
13 |
10 |
0 to 11 |
9 to 12 |
|
14 |
11 |
0 to 11 |
10 to 13 |
|
15 |
12 |
0 to 11 |
11 to 14 |
|
16 |
13 |
0 to 15 |
12 to 15 |
From this it can be seen that the last 4 words get hashed a either 3 or 4 times according to their alignment.
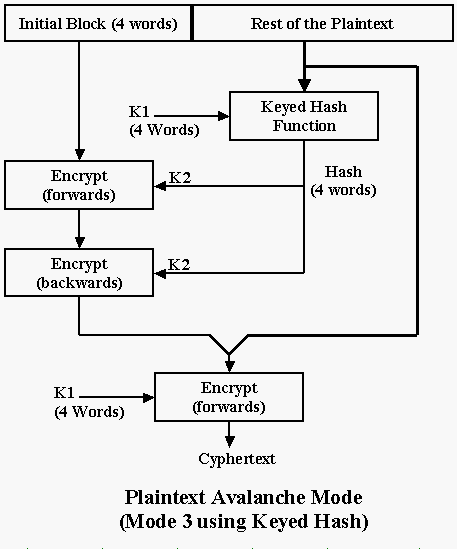
The Keyed Hash output carries the avalanche of all the plaintext bits - except for the initial block. The avalanche is then transferred to the doubly encrypted initial block. (The forward and backward encryption of the initial block ensures full avalanche of the initial block itself) Finally, the encryption of the encrypted initial block followed by the rest of the plaintext carries the avalanche through to the whole of the cyphertext.
Although this simple version of WAKE may be considered a weak cipher, this particular mode of use can be considered a crypto primitive - a plaintext avalanche function. The only other example (known to the author) is in Peter Gutmann's Secure Filing System.
There are restrictions on the use of this primitive - mainly due to its need to process all of the plaintext and have error-free transmission. This precludes its use in real-time voice and video encryption systems.
© November 1999, Keith Lockstone
Comments welcome: Keith
Back to home page
block,cipher,block cipher,crypto,cryptography,cipher design,
encryption,word auto key,word autokey,WAKE,Hereward,David Wheeler,
czczcz,DJ Wheeler,David J Wheeler